In questo articolo analizzeremo le funzioni CBAC del Cisco IOS Firewall procedendo con un esercizio che fa riferimento ad un possibile caso reale.
Schema
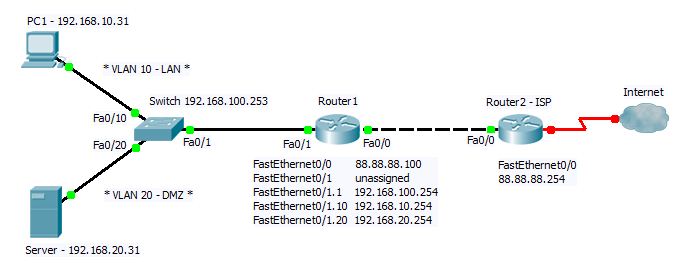
Obbiettivi:
ROUTER
- Configurazione ssh ed aaa con utente locale "Cisco" e password "Cisco1234";
- password di enable "netsetup1234"
- Consentire il management tramite SSH dalla sola LAN.
- Effettuare un minimo di Security Audit.
- Fare in modo che il PC della Lan si presenti con IP pubblico 88.88.88.103, mentre il Server in Dmz navighi con ip 88.88.88.203
- Configurare un syslog server sul Server.
- Configurazione di filtering con Firewall CBAC (2 Acl per ogni interfaccia + Cbac) come richiesto nei punti 3 e 4.
SWITCH
- Configurazione di 2 Vlan: Vlan 10 (LAN) e Vlan 20 (DMZ).
PC
- Dovrà poter fare dei ping ma non essere pingato.
- Deve poter navigare (http e https) solo con dns 208.67.222.222 (opendns) e deve poter effettuare connessioni ssh.
- Deve poter effettuare sessioni ftp SOLO verso il Server in DMZ.
- Deve poter inviare e scaricare le mail SOLO dal server in DMZ (pop3 , Smtp).
- Tutto il resto dovrà essere negato.
Server
- Dovrà pingare verso l' esterno ma non verso la Lan (PC).
- Deve farsi pingare dalla Lan.
- Dovrà dare un servirzio ftp su ip 88.88.88.203.
- Dovrà dare un servizio http su ip 88.88.88.203 porta 8080.
- Dovrà dare un servizio di posta su Pop3 e Smtp
- Deve poter navigare (http e https) solo con dns 208.67.222.222 (opendns).
- Nulla deve essere permesso verso la Lan (PC).
- Tutto il resto dovrà essere negato.
Configurazione Router
Configurazione interfacce
hostname Router1
!
interface FastEthernet0/0
description WAN to ISP
ip address 88.88.88.100 255.255.255.0
ip access-group WAN-IN in
ip access-group WAN-OUT out
ip nat outside
!
interface FastEthernet0/1
no ip address
duplex auto
speed auto
!
interface FastEthernet0/1.1
encapsulation dot1Q 1 native
ip address 192.168.100.254 255.255.255.0
!
interface FastEthernet0/1.10
encapsulation dot1Q 10
description LAN
ip address 192.168.10.254 255.255.255.0
ip access-group LAN-IN in
ip access-group LAN-OUT out
ip nat inside
!
interface FastEthernet0/1.20
encapsulation dot1Q 20
description DMZ
ip address 192.168.20.254 255.255.255.0
ip access-group DMZ-IN in
ip access-group DMZ-OUT out
ip nat inside
Configurazione aaa con utente locale "Cisco" e password "Cisco1234"; password di enable "netsetup1234".
enable secret netsetup1234
!
aaa new-model
aaa authentication login default local
!
username Cisco privilege 15 secret Cisco1234
Configurazione SSH
ip domain-name netsetup.it
crypto key generate rsa modulus 1024
!
ip ssh version 2
ip ssh time-out 60
ip ssh authentication-retries 2
!
line vty 0 4
login local
transport input ssh
Configurazione NAT e default route
ip access-list standard NAT4LAN
permit host 192.168.10.31
ip access-list standard NAT4DMZ
permit host 192.168.20.31
!
ip nat pool NATPOOL-DMZ 88.88.88.203 88.88.88.203 netmask 255.255.255.0
ip nat pool NATPOOL-LAN 88.88.88.103 88.88.88.103 netmask 255.255.255.0
!
ip nat inside source list NAT4DMZ pool NATPOOL-DMZ overload
ip nat inside source list NAT4LAN pool NATPOOL-LAN overload
!
ip route 0.0.0.0 0.0.0.0 88.88.88.254
ACL per SSH
access-list standard MGM_SSH
permit 192.168.10.0 0.0.0.255
deny any log
!
line vty 0 4
access-class MGM_SSH in
ACL LAN IN (traffico entrante sull'interfaccia LAN, in uscita verso l'esterno)
ip access-list extended LAN-IN
!
remark Ping da PC
permit icmp host 192.168.10.31 any echo
!
remark Il PC non deve rispondere ai Ping
deny icmp host 192.168.10.31 any
!
remark Navigazione PC
permit tcp host 192.168.10.31 any eq www
permit tcp host 192.168.10.31 any eq 443
permit udp host 192.168.10.31 host 208.67.222.222 eq domain
!
remark SSH da PC
permit tcp host 192.168.10.31 any eq 22
!
remark FTP da PC a Server in DMZ
permit tcp host 192.168.10.31 host 192.168.20.31 eq ftp
!
remark Posta da PC a Server in DMZ
permit tcp host 192.168.10.31 host 192.168.20.31 eq pop3
permit tcp host 192.168.10.31 host 192.168.20.31 eq smtp
!
deny ip any any
ACL LAN OUT (traffico uscente dall'interfaccia LAN verso la rete interna)
ip access-list extended LAN-OUT
!
remark Filtri Icmp
!
permit icmp any 192.168.10.0 0.0.0.255 echo-reply
permit icmp any 192.168.10.0 0.0.0.255 source-quench
permit icmp any 192.168.10.0 0.0.0.255 any packet-too-big
permit icmp any 192.168.10.0 0.0.0.255 parameter-problem
!
deny ip any any
ACL DMZ IN (traffico entrante sull'interfaccia DMZ, in uscita verso LAN e WAN)
ip access-list extended DMZ-IN
!
remark Blocco Ping da Server a LAN
deny icmp host 192.168.20.31 192.168.10.0 0.0.0.255 echo
!
remark Ping dal server e risposte ping dal Server alla LAN
permit icmp host 192.168.20.31 any echo
permit icmp host 192.168.20.31 192.168.10.0 0.0.0.255 echo-reply
!
remark Navigazione dal Server
permit udp host 192.168.20.31 host 208.67.222.222 eq domain
permit tcp host 192.168.20.31 any eq www
permit tcp host 192.168.20.31 any eq 443
!
remark Posta Server
permit tcp host 192.168.20.31 any eq pop3
permit tcp host 192.168.20.31 any eq smtp
!
deny ip any any
ACL DMZ OUT (traffico uscente dall'interfaccia DMZ verso il server)
ip access-list extended DMZ-OUT
!
remark Filtri Icmp
permit icmp 192.168.10.0 0.0.0.255 192.168.20.0 0.0.0.255 echo
permit icmp any 192.168.20.0 0.0.0.255 echo-reply
permit icmp any 192.168.20.0 0.0.0.255 source-quench
permit icmp any 192.168.20.0 0.0.0.255 any packet-too-big
permit icmp any 192.168.20.0 0.0.0.255 parameter-problem
!
remark Apertura servizi pubblici
permit tcp any host 192.168.20.31 eq 80
permit tcp any host 192.168.20.31 eq 20
permit tcp any host 192.168.20.31 eq 21
permit tcp any host 192.168.20.31 eq 25
permit tcp any host 192.168.20.31 eq 110
!
deny ip any any log
ACL WAN IN
ip access-list extended WAN-IN
!
remark Filtri Icmp
permit icmp any host 88.88.88.103 echo-reply
permit icmp any host 88.88.88.103 source-quench
permit icmp any host 88.88.88.103 paramet
!
permit icmp any host 88.88.88.203 echo-reply
permit icmp any host 88.88.88.203 source-quench
permit icmp any host 88.88.88.203 paramet
!
permit tcp any host 88.88.88.203 eq 80
permit tcp any host 88.88.88.203 eq 20
permit tcp any host 88.88.88.203 eq 21
permit tcp any host 88.88.88.203 eq 25
permit tcp any host 88.88.88.203 eq 110
!
deny icmp any any log
deny udp any any log
deny tcp any any log
deny ahp any any log
deny esp any any log
deny gre any any log
deny ip any any log
ACL WAN OUT
ip access-list extended WAN-OUT
!
remark Filtri Icmp
!
permit icmp host 88.88.88.103 any echo
permit icmp host 88.88.88.103 any parameter-problem
permit icmp host 88.88.88.103 any packet-too-big
permit icmp host 88.88.88.103 any source-quench
!
permit icmp host 88.88.88.203 any echo
permit icmp host 88.88.88.203 any parameter-problem
permit icmp host 88.88.88.203 any packet-too-big
permit icmp host 88.88.88.203 any source-quench
!
deny icmp host 88.88.88.103 any log
!
deny icmp host 88.88.88.203 any log
!
remark Filtri servizi comuni
permit tcp host 88.88.88.103 any eq 80
permit tcp host 88.88.88.103 any eq 443
permit tcp host 88.88.88.103 any eq 22
!
permit tcp host 88.88.88.203 any eq 80
permit tcp host 88.88.88.203 any eq 443
permit tcp host 88.88.88.203 any eq 25
permit tcp host 88.88.88.203 any eq 110
!
permit udp host 88.88.88.103 host 208.67.222.222 eq 53
!
permit udp host 88.88.88.203 host 208.67.222.222 eq 53
!
deny ip any any log
Abilitazione SYSLOG verso il Server
logging 192.168.20.31
logging trap informational
!
logging userinfo
!
!
enable secret 5 $1$mERr$ScvbPwxglxKfH5L8SNSQ21
!
!
!
!
!
aaa new-model
!
aaa authentication login default local
!
!
!
!
!
!
!
username Cisco privilege 15 secret 5 $1$mERr$PAHXHKWVIHlI7I.cF15hN1
!
!
!
!
!
no ip domain-lookup
ip domain-name netsetup.it
!
!
!
!
!
!
interface FastEthernet0/0
description WAN to ISP
ip address 88.88.88.100 255.255.255.0
ip nat outside
duplex auto
speed auto
!
interface FastEthernet0/1
no ip address
duplex auto
speed auto
!
interface FastEthernet0/1.1
encapsulation dot1Q 1 native
ip address 192.168.100.254 255.255.255.0
!
interface FastEthernet0/1.10
encapsulation dot1Q 10
ip address 192.168.10.254 255.255.255.0
ip access-group LAN-IN in
ip nat inside
!
interface FastEthernet0/1.20
encapsulation dot1Q 20
ip address 192.168.20.254 255.255.255.0
ip access-group DMZ-IN in
ip nat inside
!
interface Vlan1
no ip address
shutdown
!
ip nat pool NATPOOL-DMZ 88.88.88.203 88.88.88.203 netmask 255.255.255.0
ip nat pool NATPOOL-LAN 88.88.88.103 88.88.88.103 netmask 255.255.255.0
ip nat inside source list NAT4DMZ pool NATPOOL-DMZ overload
ip nat inside source list NAT4LAN pool NATPOOL-LAN overload
ip classless
ip route 0.0.0.0 0.0.0.0 88.88.88.254
!
!
ip access-list standard NAT4LAN
permit host 192.168.10.31
ip access-list standard NAT4DMZ
permit host 192.168.20.31
ip access-list standard MNG-SSH
permit 192.168.10.0 0.0.0.255
deny any
ip access-list extended LAN-IN
remark PC1 pinga ma non deve essere pingato
permit icmp host 192.168.10.31 any echo
deny icmp host 192.168.10.31 any
remark Navigazione PC1
permit tcp host 192.168.10.31 any eq www
permit tcp host 192.168.10.31 any eq 443
permit udp host 192.168.10.31 host 208.67.222.222 eq domain
remark SSH da PC1
permit tcp host 192.168.10.31 any eq 22
remark FTP da PC1 a Server in DMZ
permit tcp host 192.168.10.31 host 192.168.20.31 eq ftp
remark Posta da PC1 verso Server in DMZ
permit tcp host 192.168.10.31 host 192.168.20.31 eq pop3
permit tcp host 192.168.10.31 host 192.168.20.31 eq smtp
ip access-list extended DMZ-IN
remark Ping dal Server in DMZ
deny icmp host 192.168.20.31 192.168.10.0 0.0.0.255 echo
permit icmp host 192.168.20.31 any echo
permit icmp host 192.168.20.31 192.168.10.0 0.0.0.255 echo-reply
remark Navigazione dal Server
permit udp host 192.168.20.31 host 208.67.222.222 eq domain
permit tcp host 192.168.20.31 any eq www
permit tcp host 192.168.20.31 any eq 443
remark Posta Server
permit tcp host 192.168.20.31 any eq pop3
permit tcp host 192.168.20.31 any eq smtp
remark Tutto il resto negato
deny ip any any
!
!
!
!
!
logging 192.168.20.31
line con 0
logging synchronous
login
line vty 0 4
access-class MNG-SSH in
login
login authentication default
transport input ssh
!
!
!
end
Router1#
Router1 con0 is now available
Press RETURN to get started.
User Access Verification
Username: Cisco
Password:
Router1>en
Password:
Router1#%SYS-5-PRIV_AUTH_PASS: Privilege level set to 15 by Cisco
Router1#sh
Router1#show runn
Router1#show running-config
Building configuration...
Current configuration : 2931 bytes
!
version 12.4
no service timestamps log datetime msec
no service timestamps debug datetime msec
no service password-encryption
!
hostname Router1
!
logging userinfo
!
!
enable secret 5 $1$mERr$ScvbPwxglxKfH5L8SNSQ21
!
!
!
!
!
aaa new-model
!
aaa authentication login default local
!
!
!
!
!
!
!
username Cisco privilege 15 secret 5 $1$mERr$PAHXHKWVIHlI7I.cF15hN1
!
!
!
!
!
no ip domain-lookup
ip domain-name netsetup.it
!
!
!
!
!
!
interface FastEthernet0/0
description WAN to ISP
ip address 88.88.88.100 255.255.255.0
ip nat outside
duplex auto
speed auto
!
interface FastEthernet0/1
no ip address
duplex auto
speed auto
!
interface FastEthernet0/1.1
encapsulation dot1Q 1 native
ip address 192.168.100.254 255.255.255.0
!
interface FastEthernet0/1.10
encapsulation dot1Q 10
ip address 192.168.10.254 255.255.255.0
ip access-group LAN-IN in
ip nat inside
!
interface FastEthernet0/1.20
encapsulation dot1Q 20
ip address 192.168.20.254 255.255.255.0
ip access-group DMZ-IN in
ip nat inside
!
interface Vlan1
no ip address
shutdown
!
ip nat pool NATPOOL-DMZ 88.88.88.203 88.88.88.203 netmask 255.255.255.0
ip nat pool NATPOOL-LAN 88.88.88.103 88.88.88.103 netmask 255.255.255.0
ip nat inside source list NAT4DMZ pool NATPOOL-DMZ overload
ip nat inside source list NAT4LAN pool NATPOOL-LAN overload
ip classless
ip route 0.0.0.0 0.0.0.0 88.88.88.254
!
!
ip access-list standard NAT4LAN
permit host 192.168.10.31
ip access-list standard NAT4DMZ
permit host 192.168.20.31
ip access-list standard MNG-SSH
permit 192.168.10.0 0.0.0.255
deny any
ip access-list extended LAN-IN
remark PC1 pinga ma non deve essere pingato
permit icmp host 192.168.10.31 any echo
deny icmp host 192.168.10.31 any
remark Navigazione PC1
permit tcp host 192.168.10.31 any eq www
permit tcp host 192.168.10.31 any eq 443
permit udp host 192.168.10.31 host 208.67.222.222 eq domain
remark SSH da PC1
permit tcp host 192.168.10.31 any eq 22
remark FTP da PC1 a Server in DMZ
permit tcp host 192.168.10.31 host 192.168.20.31 eq ftp
remark Posta da PC1 verso Server in DMZ
permit tcp host 192.168.10.31 host 192.168.20.31 eq pop3
permit tcp host 192.168.10.31 host 192.168.20.31 eq smtp
ip access-list extended DMZ-IN
remark Ping dal Server in DMZ
deny icmp host 192.168.20.31 192.168.10.0 0.0.0.255 echo
permit icmp host 192.168.20.31 any echo
permit icmp host 192.168.20.31 192.168.10.0 0.0.0.255 echo-reply
remark Navigazione dal Server
permit udp host 192.168.20.31 host 208.67.222.222 eq domain
permit tcp host 192.168.20.31 any eq www
permit tcp host 192.168.20.31 any eq 443
remark Posta Server
permit tcp host 192.168.20.31 any eq pop3
permit tcp host 192.168.20.31 any eq smtp
remark Tutto il resto negato
deny ip any any
!
!
!
!
!
logging 192.168.20.31
line con 0
logging synchronous
login
line vty 0 4
access-class MNG-SSH in
login
login authentication default
transport input ssh
!
!
!
end


